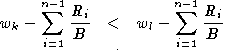
Next: References
Up: Receiver-driven Bandwidth Adaptation
Previous: Acknowledgements
We present a proof of correctness of the signal mapping algorithm
detailed in Section 2.3. We use the same notation introduced
in Section 2.3.
Claim:
This signal layer mapping meets the following constraints:
- The network channel limits are observed.
- No source Sk transmits more than its total share, wkB.
- wk >= wj implies that Ak,n <= Aj,n forall n
Proof:
In the proof we refer to line numbers in the algorithm detailed in
Figure 6.
-
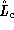 represents the unused bandwidth available in network
channel c. Thus, the check in line 15 guarantees
that no source
will cause the rate limit of a network channel to be exceeded
represents the unused bandwidth available in network
channel c. Thus, the check in line 15 guarantees
that no source
will cause the rate limit of a network channel to be exceeded
-
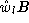 represents the portion of the bandwidth share of source Sl
that has not been utilized by the source. Thus, the decrementing
of
represents the portion of the bandwidth share of source Sl
that has not been utilized by the source. Thus, the decrementing
of 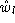 in line 21, along with the check in
line 12, guarantees that
no source will transmit more that its total share, which is
wlB.
in line 21, along with the check in
line 12, guarantees that
no source will transmit more that its total share, which is
wlB.
- The algorithm iterates through the average weight list
looking for the largest remaining weight,
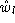 . Now assume
that for the two sources in question Sk, and
Sj, all signal layers 1,..., n-1
have been mapped to network channels. Next
assume that the result of the algorithm's output for layer n is
such that muk,n > muj,n
. Now assume
that for the two sources in question Sk, and
Sj, all signal layers 1,..., n-1
have been mapped to network channels. Next
assume that the result of the algorithm's output for layer n is
such that muk,n > muj,n
This along with line 9 imply that

Line 21 of the algorithm implies that in order for
(1) to
hold the following must also be true:
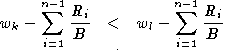
which implies that
wk < wl
Finally, the arg max
directive in line 9 furnishes us
with the bootstrap for the induction in the first iteration
which completes the proof of statement 3 of the claim. QED
Elan Amir
Sun Aug 17 23:48:24 PDT 1997
![]()